Google’s Web Store Spreads Malware Again, 100,000 Users Infected By Malicious Chrome Extensions
Security firm Radware has uncovered malicious extensions believed to infect more than 100,000 Google Chrome users. According to a report released on Thursday, malware was discovered in the browser’s official Web Store.
Using machine-learning algorithms, Radware was able to pinpoint a zero-day malware threat to one of its clients. These malicious extensions spread via links sent over Facebook, pilfering login credentials, mining cryptocurrencies, and engaging in click fraud, among others.
Cybercriminals involved with the latest malware campaign were said to have been active since March 2018. Since that time, they infected 100,000 users worldwide, the company said in its blog post. Called “Nigelthorn”— a name derived from the Nigelify application, the malware redirects victims to a fake Youtube page and prompts them to install a Chrome extension to play the video. Once installed, these computers become part of the botnet as harmful JavaScript download additional code from the command center. The infection process continues when the victim’s Facebook contacts click on the sent malicious link.
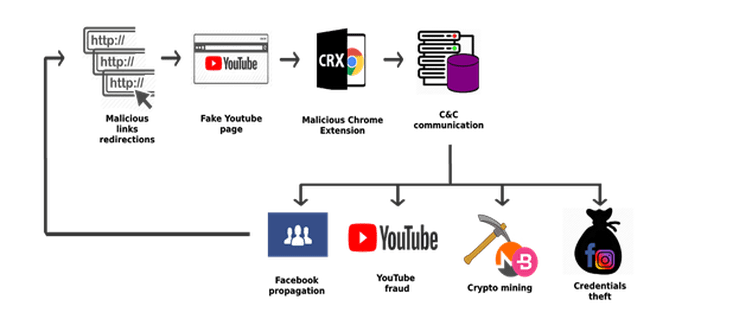
To bypass Google’s extension validation checks, attackers modified copies of legitimate extensions and added malicious script inside. Thanks to Google’s security algorithms, seven of these extensions were removed right after their discovery, including Nigelify, PwnerLike, Alt-j, Fix-case, Divinity 2 Original Sin: Wiki Skill Popup, keeprivate, and iHabno. Radware emphasized that the malware only infected Chrome users on Windows and Linux so other browsers are unaffected by the attack.
Radware pointed out that the malware went undetected despite tight security over the network. The firm also warned that attackers might identify other ways to bypass security controls with mutated malware disguised as browser plug-ins. And it seemed that bad Chrome extensions are one of Google’s weak spots.
Meanwhile, Trend Micro has identified the return of FacexWorm, a malicious extension that propagates via socially engineered links on Facebook Messenger similar to Digmine. Apart from stealing credentials, FacexWorm redirects potential victims to cryptocurrency scams and referral links of attackers, installs bad mining codes, and takes over transactions on trading platforms and in web wallets. It was first spotted in August of last year but resurfaced recently in certain countries.
In January, analytics firm ICEBRG identified four extensions that were likely used in a click-fraud scam to generate revenue. These were removed from the Web Store once discovered, but not after infecting 500,000 Chrome users.
Despite being regarded as one of the safest browsers, Chrome is far from being invulnerable. Attackers continue to work around security protocols through third-party extensions loaded with malicious codes. Chrome users should verify an extension before installing it. That, or just stay away from third-party providers, even if they’ve been vetted by Google’s stringent security process.
[Featured image via Pixabay]



